Most people have more than one email address. While Gmail is popular, many people have multiple Gmail accounts or hang on to old accounts, like America Online (AOL) or Hotmail. To streamline their email management, these people may use an email app to receive and send all emails from a single location.
Security teams want the same experience to manage their complex cybersecurity technology stack from a centralized hub. To maintain their competitive edge, security vendors must integrate their solutions with everything else in the customer’s environment, including tools that augment their capabilities. As the security tool’s user base grows, the number of integrations needs to scale in parallel.
To extend the value of a security tool’s capabilities, companies must streamline how their solutions integrate with the other tools across an increasingly complex cybersecurity technology stack.
The Current State of Security Technology Stacks
As much as cybersecurity tool sprawl poses a challenge for CISOs, it poses an even greater challenge for security solution vendors who need to maintain their competitive edge in an increasingly crowded market.
Solution Augmentation
Depending on the research reviewed, organizations incorporate anywhere from 70 to 130 discrete tools to manage security. For each solution to remain competitive, it must integrate with all the other tools across all the different categories of security controls. Building individual integrations for every security team use case and adjacent technology becomes overwhelming.
A significantly simplified version of a single SIEM’s integration and the different tools that need to communicate with each other could look like this:
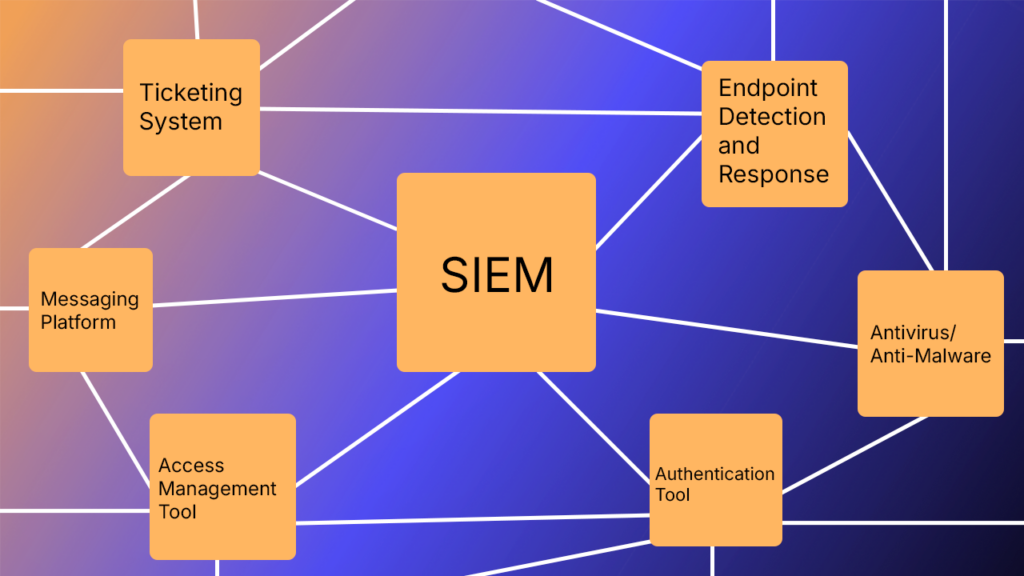
Security vendors struggle to integrate with a customer’s centralized security hub and the other technologies each customer uses.
For example, security teams often use a combination of a ticketing system, like Jira, and a communication platform, like Microsoft Teams, to track their incident response activities. In this case, a security information and event management (SIEM) tool needs to build an integration with both of those for seamless communication. Meanwhile, the messaging platform and the ticketing system must communicate to ensure real-time incident response tracking.
None of these tools compete, but they augment each other when connected across the customer’s complex security ecosystem.
Adjacent (Competitor) Technologies
Some security vendors offer a variety of solutions addressing different security controls. For example, a single vendor might help customers manage vulnerability scanning, endpoint security, and cloud security. Integrating with competitors undermines the company’s business model.
Simultaneously, customers may not want to buy into a vendor’s entire ecosystem. A customer may find that the vulnerability scanning solution meets its needs while looking for a different cloud security solution. In these cases, the lack of integration might lead customers to a different, albeit less perfect, vulnerability scanning solution.
To achieve sales and revenue targets, security vendors may need to expand their integration capabilities, even if it means giving customers the option of choosing competitors.
What Is a Unified Security API?
The fundamental idea behind a unified API is that it aggregates multiple APIs under a general software category. It provides a single, standardized endpoint that makes integration easier across diverse tools to normalize data and standardize API fields across vendors.
For example, in cybersecurity, these aggregations might look like the different categories of security controls, including:
- Alerting and event management
- Incident response communications
- Vulnerability management
- Data storage
- Identity and access management
- Network security
- Asset management
- Endpoint security
- Cloud security
- Email security
Within each category, the platform parses data and normalizes it against a vendor-agnostic schema, like the Open Cybersecurity Schema Framework (OCSF). Focused on cross-solution interoperability, the provider enables security vendors to provide the customer integrations they want and need without having to build each one individually or build one for an adjacent, competitive technology.
Is a Unified Security API the Same as an Integration as a Service Platform (IPaaS)?
Like everything else in security, the answer to this question is, “well, that depends.” A generalized IPaaS platform often fails to meet a security vendor’s unique needs for various reasons. However, an IPaaS that understands security data formats and use cases enables vendors to improve their market share by responding to customer needs and reducing the time spent building integrations.
Various formats
The difference between general IPaaS tools and a cybersecurity-focused integration platform starts with the data transmitted between applications.
Business IPaaS
General business-level APIs primarily use JSON (JavaScript Object Notation), although they may also use:
- XML (eXtensible Markup Language)
- Form-Encoded (application/x-www-form-urlencoded)
Security Integration Platforms as a Service
However, security solutions use a variety of data formats that can include:
- Syslog
- JSON
- XML
- Vendor specific formats, like Palo Alto, Cisco, Microsoft Windows Event logs
Each of these schemas has its own:
- Field names
- Structures
- Nesting
These diverse structures and data formats make it difficult for a generalized IPaaS to parse data and enforce schemas consistently.
Schema stability and flexibility
The different use cases between business and security APIs impact their stability and flexibility.
Business Integration Platforms
Traditional APIs are easier for an integration platform to manage because the schemas are highly stable and predictable. These APIs are built around predictable use cases that center on stable entities. For example, creating an invoice or getting a list of orders pulls the same data type every time, even if the specific inputs change.
Security Integration Platforms
Meanwhile, security vendors often update their schemas regularly to respond to new threats and risks. Cybersecurity is dynamic, and the APIs reflect that. An API can break when the vendor:
- Adds new fields
- Changes field names
- Updates the entire log structure
Compliance
While business APIs transfer sensitive data, the stability of the use cases makes it easier to standardize the formatting.
Business Integration Platforms
General business API use cases have few sensitive fields, so a general IPaaS may not be able to provide the security and privacy controls necessary. At the business operational and compliance level, an IPaaS may need to consider only a few data protection compliance use cases:
- Payment Card Industry Data Security Standard (PCI DSS) for any retail or ecommerce customer
- Health Insurance Portability and Accountability Act (HIPAA) for the healthcare industry
- Sarbanes Oxley (SOX) for the financial services industry
Security Integration Platforms
By their nature, security tools generate and share many types of sensitive data. To make this more challenging, many of these are dynamic data types. Some typical data transmitted across these security APIs includes:
- IP addresses
- Hostnames
- User credentials
Synqly: The Unified Security API and Cybersecurity Focused IPaaS that Extends Your Solution’s Customer Base
Built by security veterans specifically for security vendors, Synqly addresses the use cases that our customers need. Security teams need and want integrated solutions, and we understand how to build and maintain security tool APIs. Our security-focused integration platform provides a unified API across multiple vendors within a security control category, reducing the time and resources required to deliver a broad, integrated security system.
Contact us today to see how to improve revenue with a unified security API that understands you and your customers.
